17.1.2.ThreatTest System settings
General ThreatTest System settings are available on the System settings page. To configure these settings, navigate to ThreatTest ⇒ Settings ⇒ System settings on the ribbon:
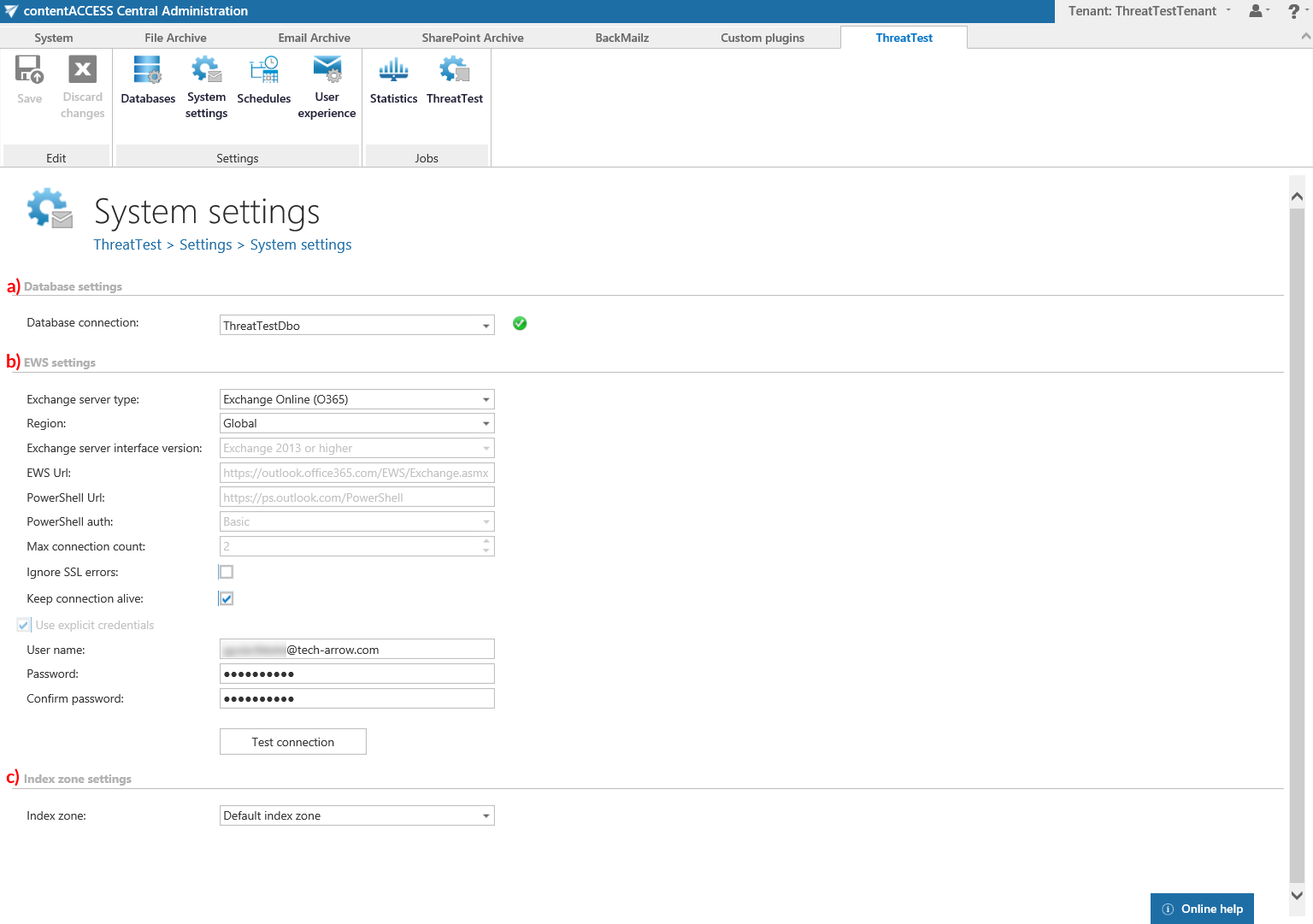
a) Database settings
Select the ThreatTest database, that you have already configured on ThreatTest ⇒ Settings ⇒ Databases page (in our case it is database “ThreatTestDbo”), from the dropdown list. This selected database will be used by the ThreatTest job and all metadata during the synchronization process will also be stored here.
b) EWS settings
Under Exchange server type and Exchange server interface version select the type and version of the server where your email provider is running. Then enter the EWS URL, PowerShell URL and the PowerShell authentication. These data must be requested from the email provider that you use (the configuration properties are the same for On-premise and Hosted Exchange).
Under Max. connection count option the user may define how many parallel connections will be maintained by the system when connecting to PowerShell.
If you do not have a valid certificate, you can check the Ignore SSL errors checkbox.
Keep connection alive: If this option is turned on, then the connection between contentACCESS and the Exchange server is cached, which increases the performance. If the Exchange is load balanced, some requests can land on another Exchange, which causes errors in contentACCESS. In these cases unchecking the Keep connection alive option will destroy the connection after each request and will rebuild it on the next request.
- If you are communicating with one Exchange server: turn it on to increase the performance
- If you have a load balanced Exchange environment and there are communication problems with the Exchange: it is recommended to turn it off
Further enter the applicable User name and Password to connect to the Exchange (use explicit credentials or log in under service-credentials). The user entered here must have the necessary rights to all mailboxes that he wants to activate ThreatTest for. The necessary rights are the following:
- Full-access to all mailboxes
- View only organization management
- Org Custom Apps (this is required for add-in installation)
We recommend to run a test connection via Test button.
c) Index zone settings
Select here a previously configured Index zone that will be assigned to all items processed by the ThreatTest job.
