25.26.3.Grant permissions for Teams archive
In this section, we describe step by step how to grant permissions for the Teams archive, which enables contentACCESS to authenticate and connect to the Microsoft Dataverse environment using a modern and more secure way of authentication.
1) Navigate to your registered application (Azure Active Directory => App registration => Owned applications => registered application [Test_app in our example] => open the application by clicking on the title). On the application details page, click the API permissions button on the left menu. When the configured permissions page loads, click the + Add permission button and select the requested API.
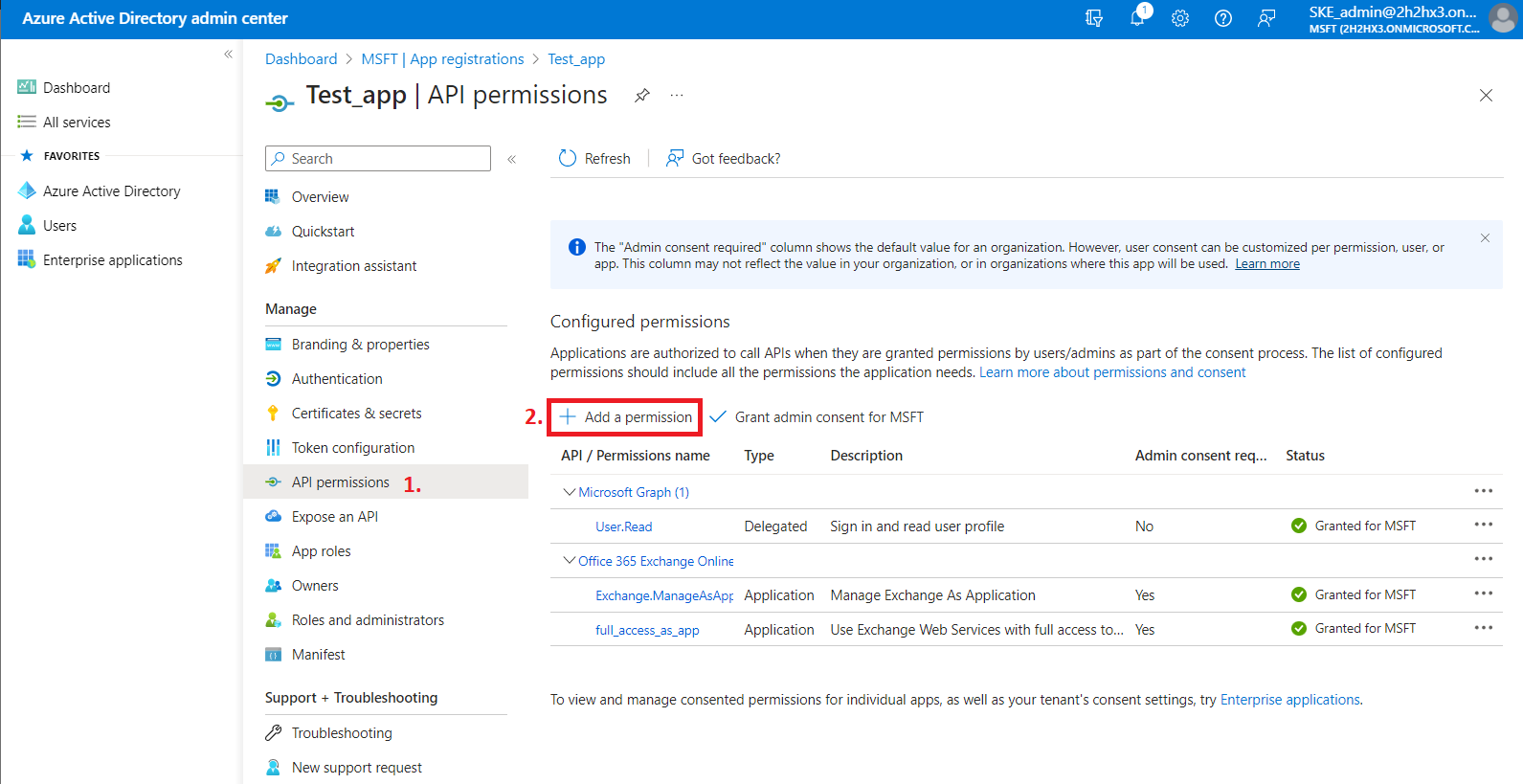
2) On the Request API permissions => Microsoft APIs tab, you need permissions from Microsoft Graph and SharePoint options. In the case of Teams archive, some permissions need to be selected from the Delegated option, and some from the Application option. The required permission set depends on the Teams Archive configuration in contentACCESS you would use.
There you can use delegated access or application access. When you choose delegated access, contenACCESS will connect and access the Teams data in the name of a superuser. This superuser MUST have owner access to every team you would like to archive.
The second approach is application access, where contentACCESS will connect to Microsoft Teams using a configured application. This application must NOT have owner access to any of the Teams, but you need to request access to Microsoft Protected API. For more information about how to request more access to Microsoft Protected API, read the following subsection, or follow the guideline here. The request is usually accepted within a day or two. The recommended approach is application access.
If you do not know at this point which approach will fit the best for you, add both permissions to the application. You can decide later during the archive configuration which option to use.
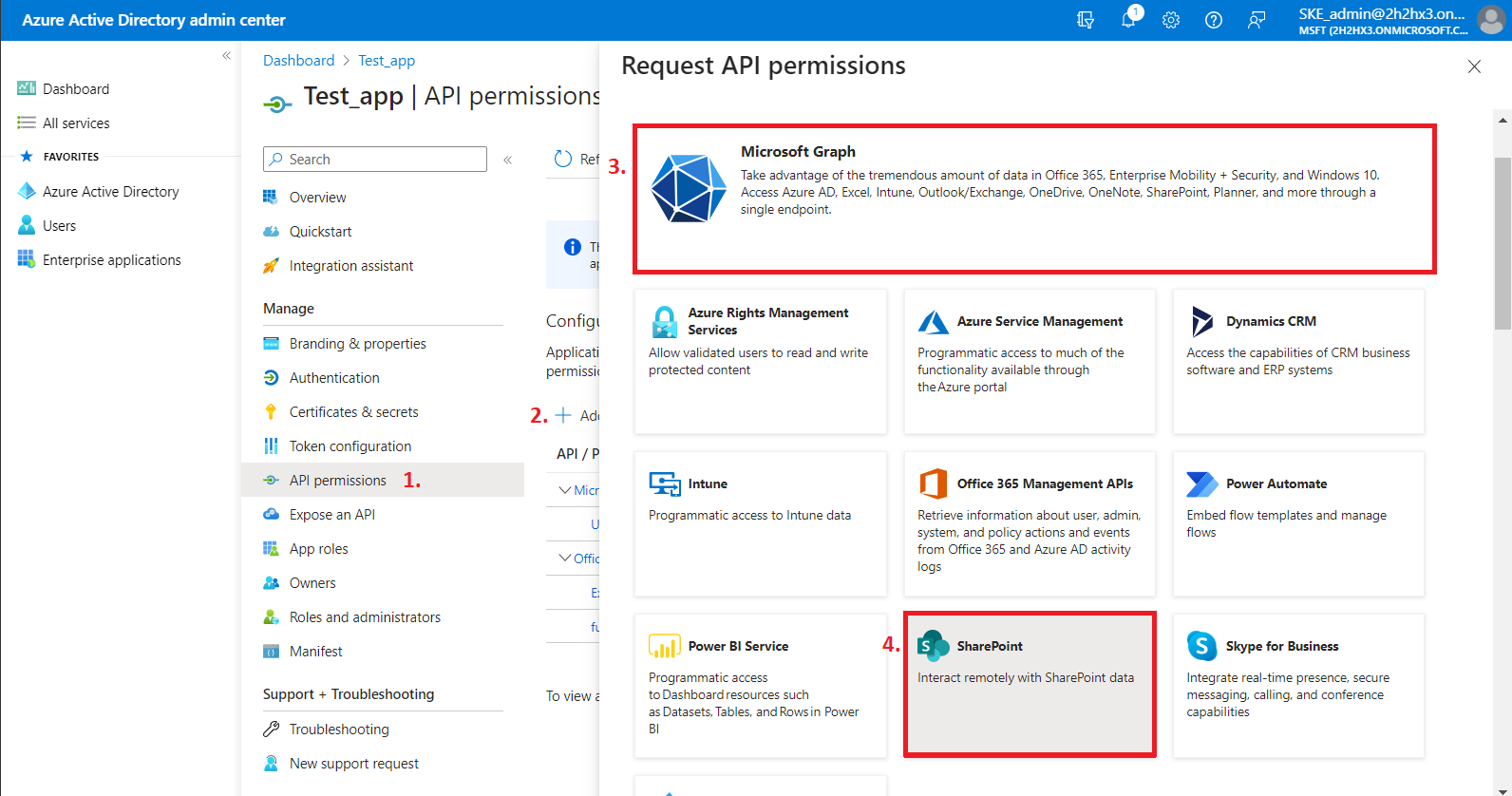
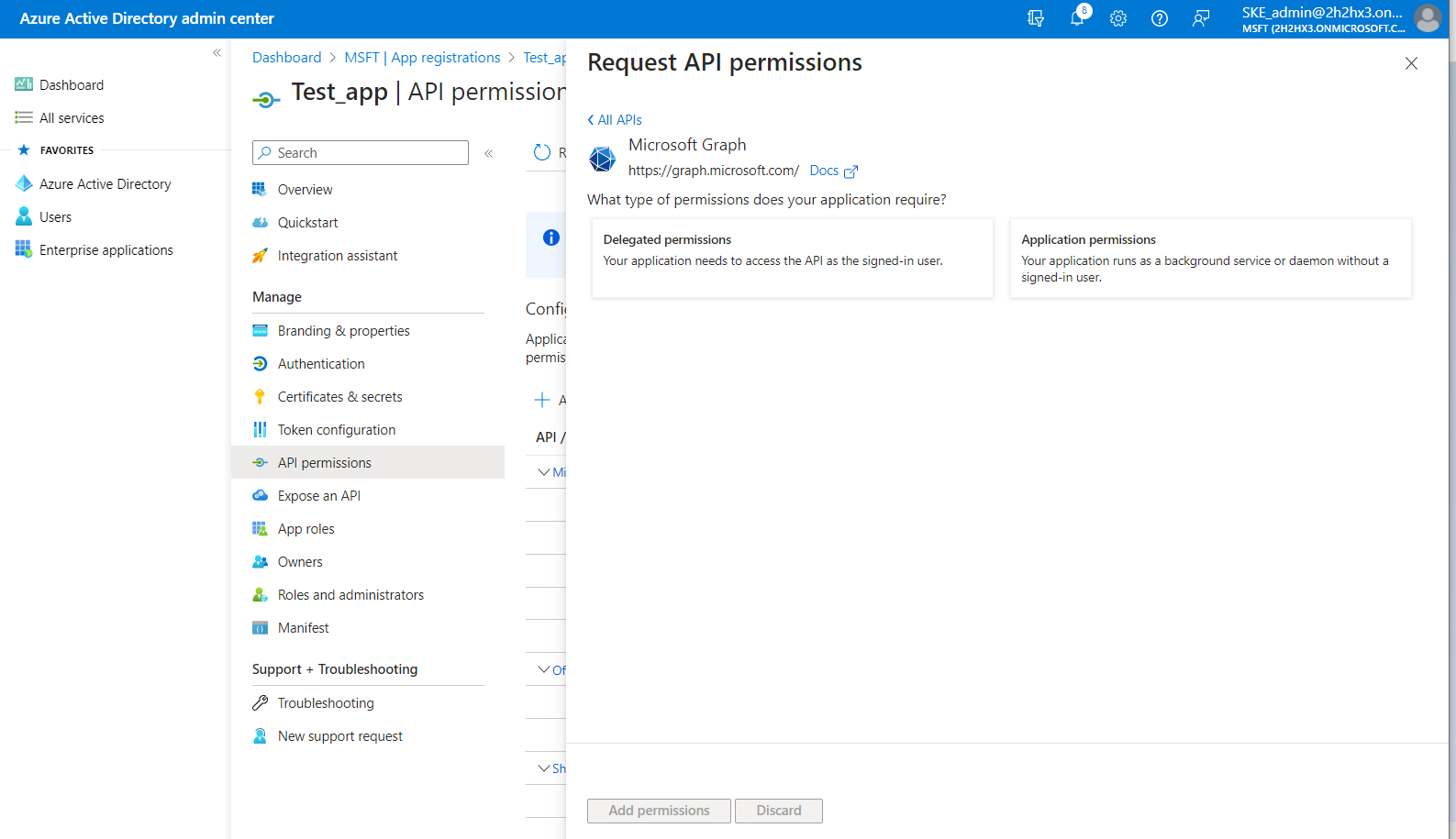
First, let’s go through the Microsoft Graph permissions. After selecting the option from the list, you need to choose the required Application and Delegated permissions from these categories.
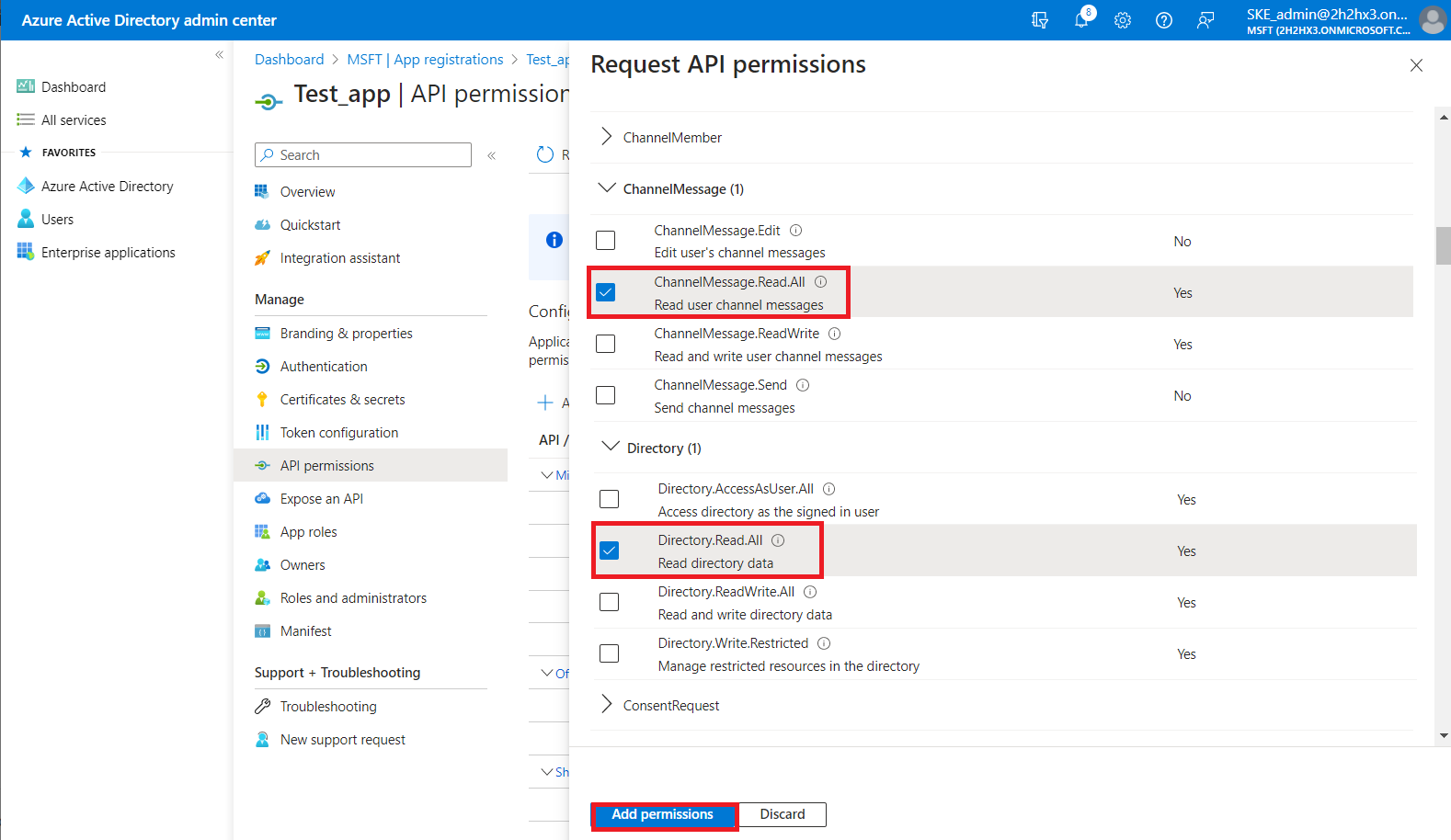
From the Delegated permissions category locate the following permissions, then click the Add permissions button:
- ChannelMessage.Read.All – Read user channel messages
- Directory.Read.All – Read directory data
- Group.ReadWrite.All – Read and write all groups
- GroupMember.Read.All – Read all group memberships
- TeamsTab.Read.All – Read tabs in Microsoft Teams
- TeamworkTag.ReadWrite – Read and write tags in Teams
- User.Read – Sign in and read user profile
From the Application permissions category locate these permissions, then click on the Add permissions button:
- ChannelMessage.Read.All – Read all channel messages
- Directory.Read.All – Read directory data
- Group.ReadWrite.All – Read and write all groups
- GroupMember.Read.All – Read all group memberships
- TeamsTab.Read.All – Read tabs in Microsoft Teams
- Teamwork.Migrate.All – Creating and managing resources for migration to Microsoft Teams
- TeamworkTag.Read.All – Read tags in Teams
From the SharePoint option, the following Delegated and Application permissions are required:
Delegated permissions
- Sites.FullControl.All – Have full control of all site collections
- Sites.Manage.All – Read and write items and lists in all site collections
- Sites.ReadWrite.All – Read and write items in all site collections
- TermStore.ReadWrite.All – Read and write managed metadata
- User.ReadWrite.All – Read and write user profiles
Application permissions
- Sites.FullControl.All – Have full control of all site collections
- Sites.Manage.All – Read and write items and lists in all site collections
- Sites.ReadWrite.All – Read and write items in all site collections
- TermStore.ReadWrite.All – Read and write managed metadata
- User.ReadWrite.All – Read and write user profiles
Click on Add permissions.
3) For delegated access, the following option must be enabled:
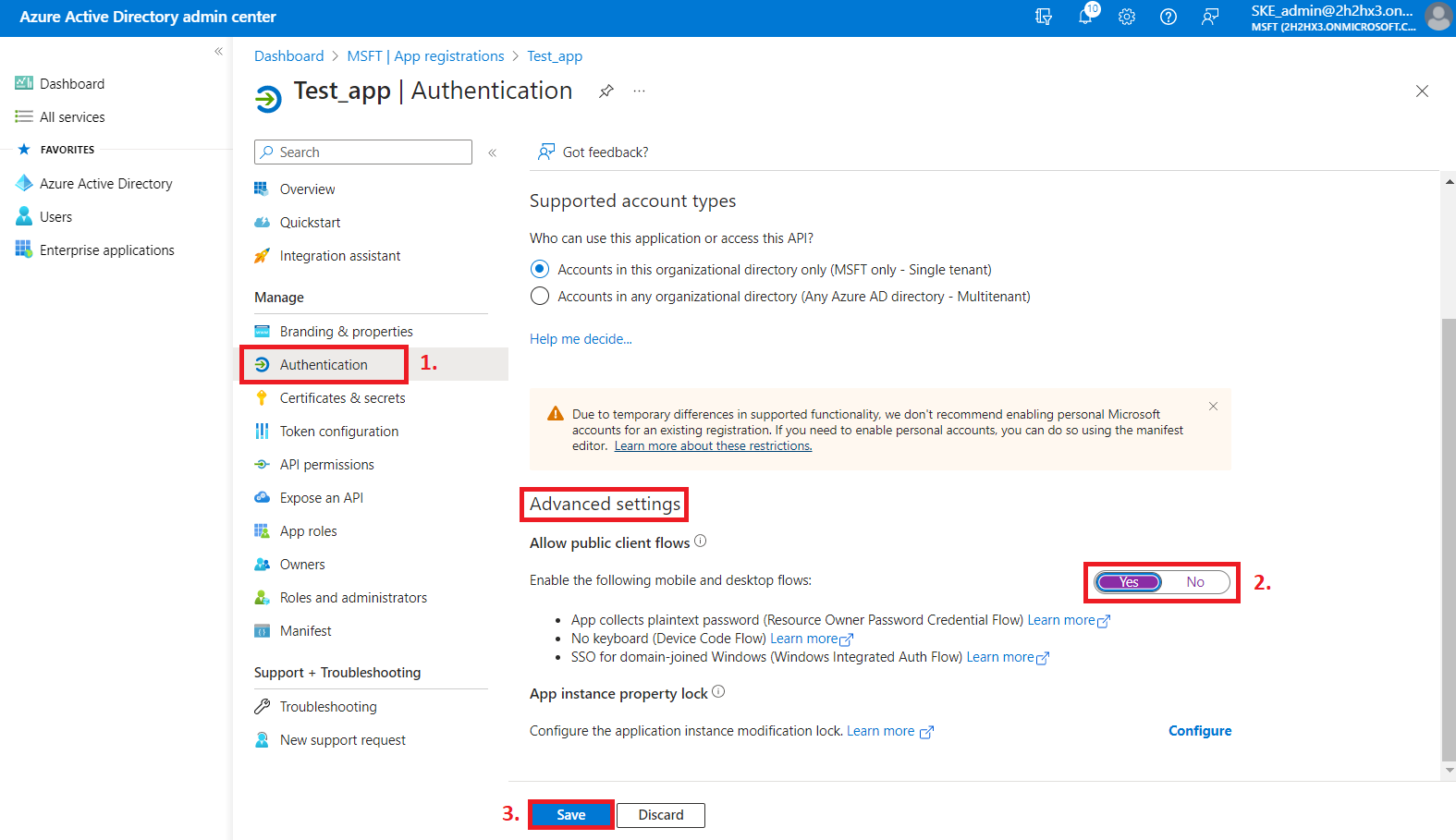
4) After the permissions have been assigned to the application, the administrator must grant consent for these permissions. Click on the Grant admin consent for “TENANTNAME” button.
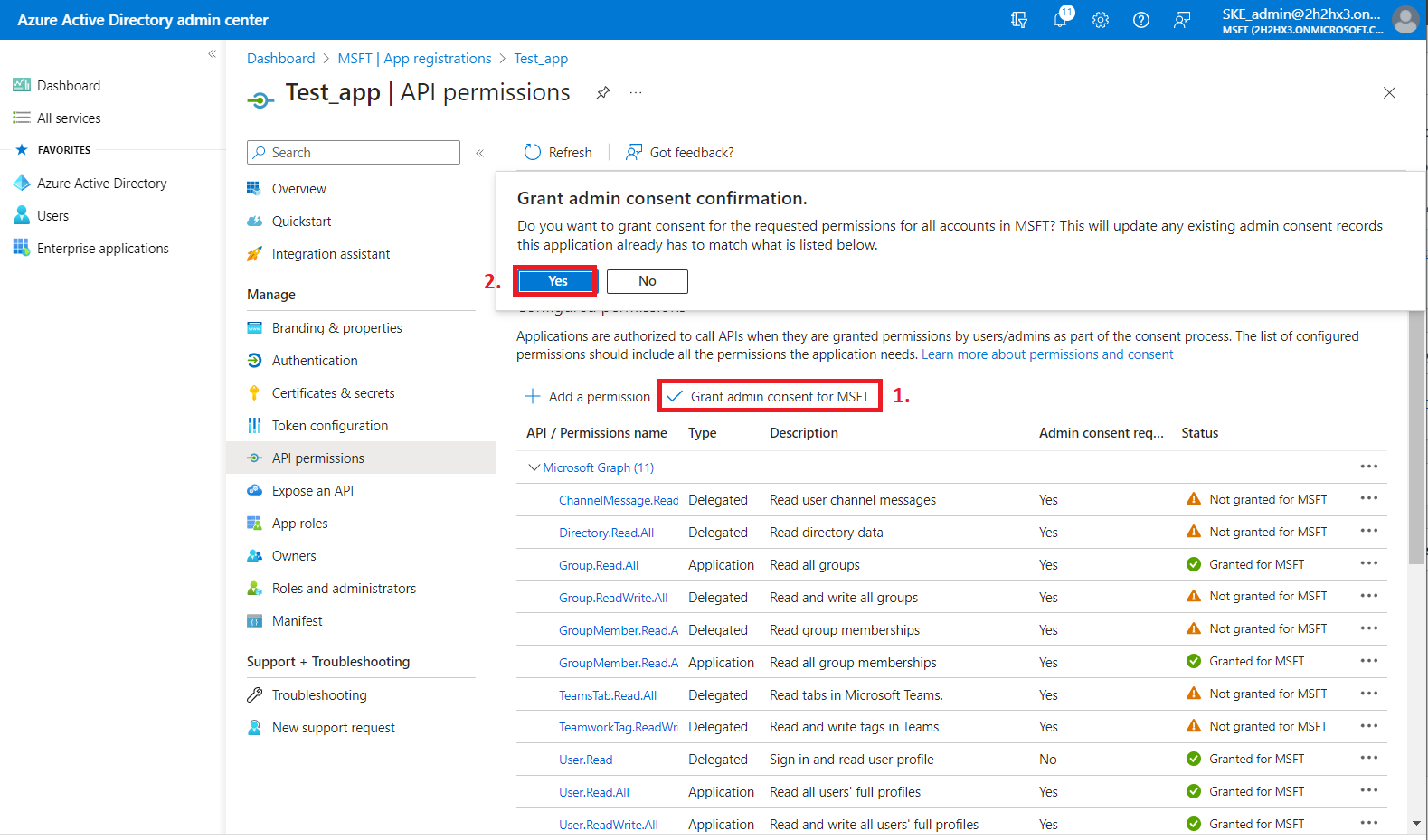
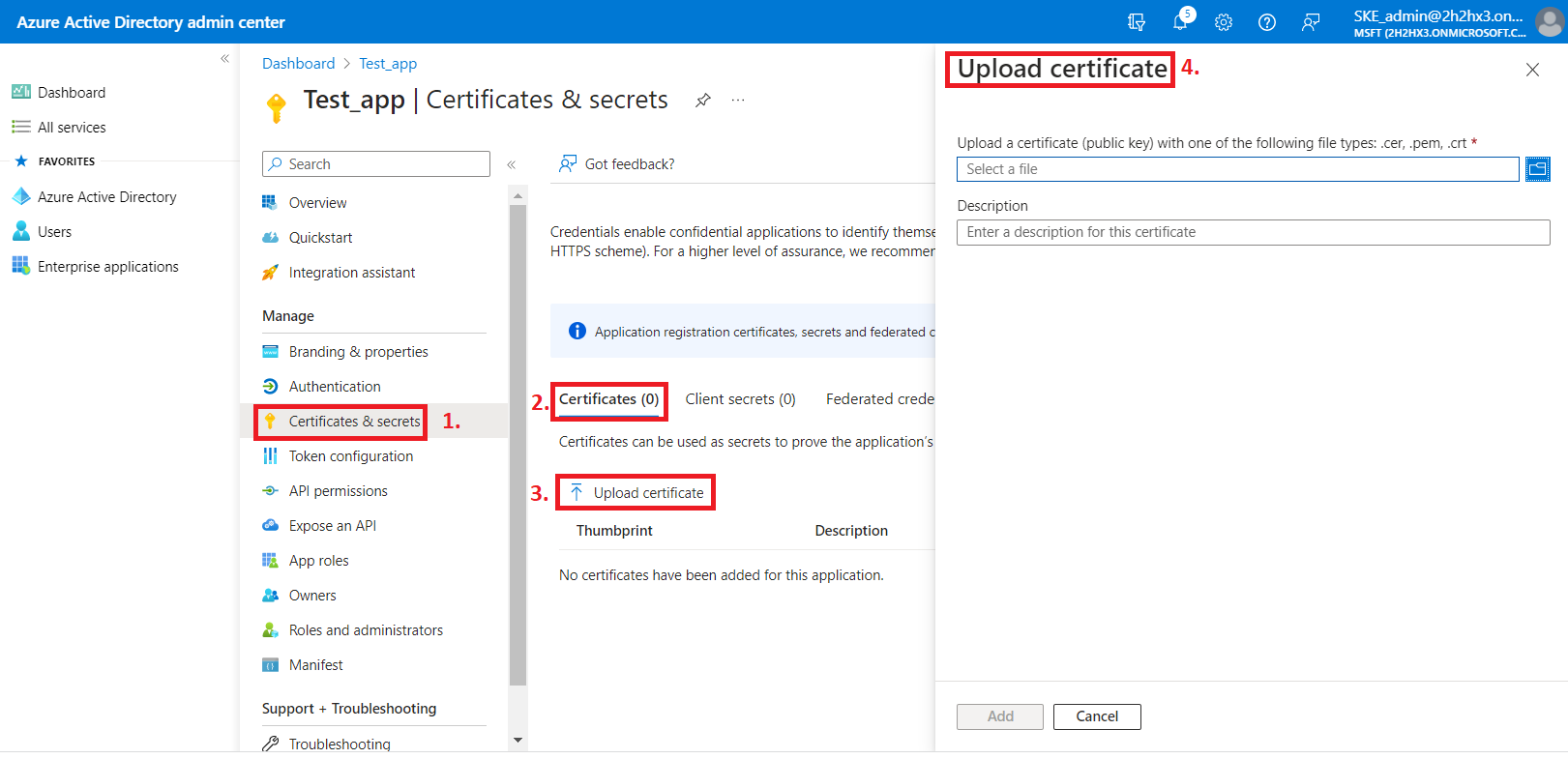
5) When the permissions are assigned to the application and the admin consent is granted, the client access certificate needs to be assigned to the application.
Click on the Certificates & secrets option in the left side menu. On the certificate management screen click on the Upload certificate (Certificates tab) button. Browse the client certificate you want to use and upload it. It can be a self-signed certificate or an already existing one. A PowerShell script for creating a self-signed certificate can be downloaded here.
6) Next, add a new client secret by clicking on the + Next client secret button. This is necessary for some plugins and client applications (Test_client secret in our example).
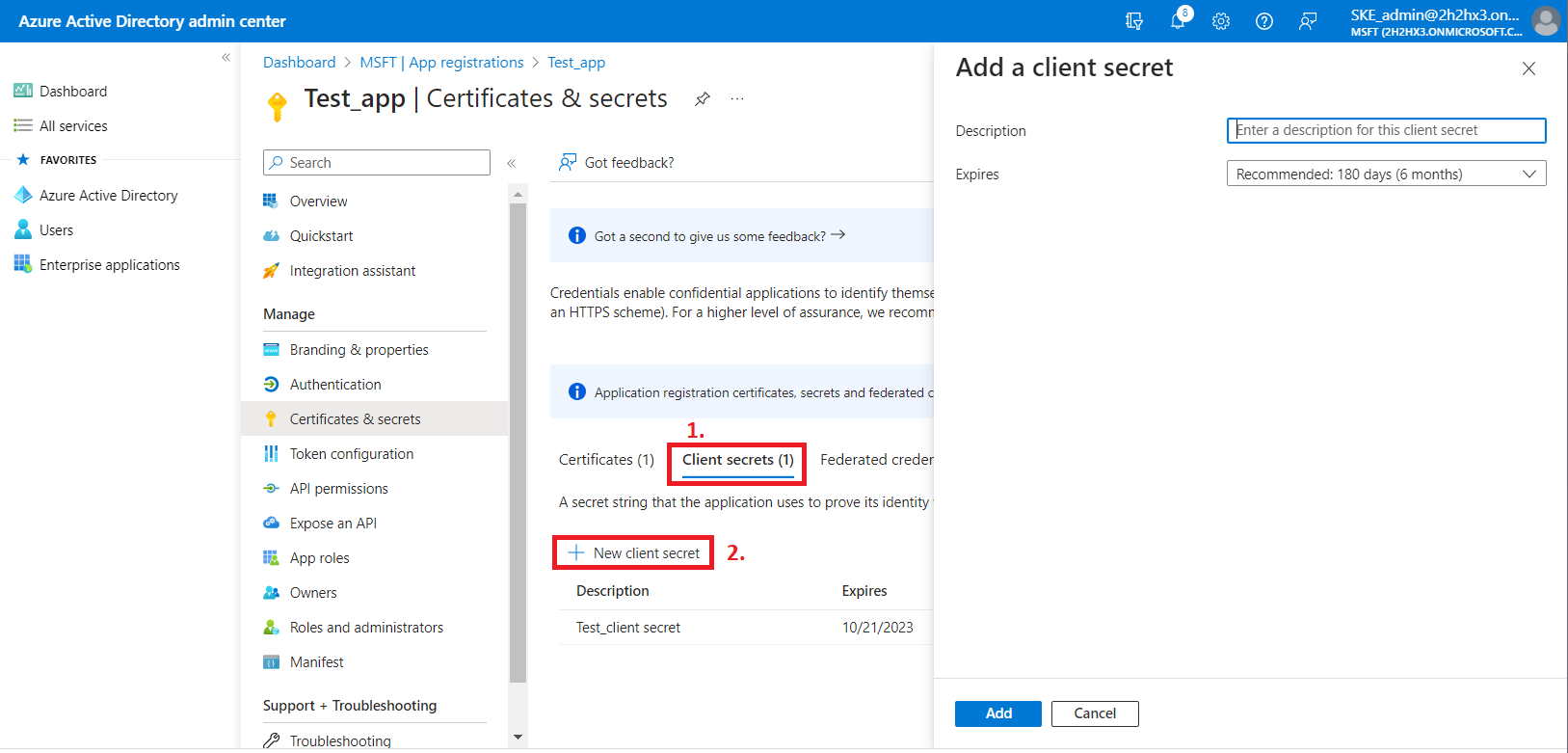
After the configuration is done, copy the client secret shown on the Get client secret dialog box to a secure location so that you can refer to it later. The client secret will be required when configuring certain contentACCESS models with modern authentication– like Email archive, SharePoint archive, Teams archive, GDPR Exchange, and Exchange connection.
